Today, I wiped and re-imaged a PC for the sake of testing… and ended up making log-on impossible. Here’s what happened.
DUO For Workstation
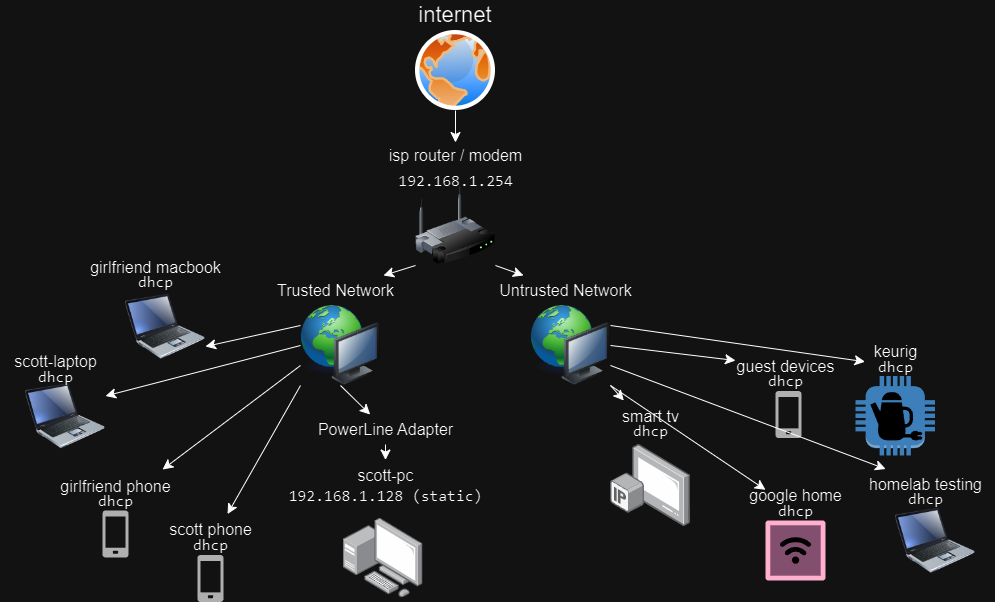
For those who don’t know, DUO has a workstation install that allows you to require push approval at the Windows log-on screen1. I thought it would be good practice to deploy this in my home environment.
I signed into the DUO Admin Portal, activated Microsoft RDP as a protected application, and made note of my API hostname, integration key, and secret key. Next, I installed the application locally and configured the local and portal-side authentication policies.
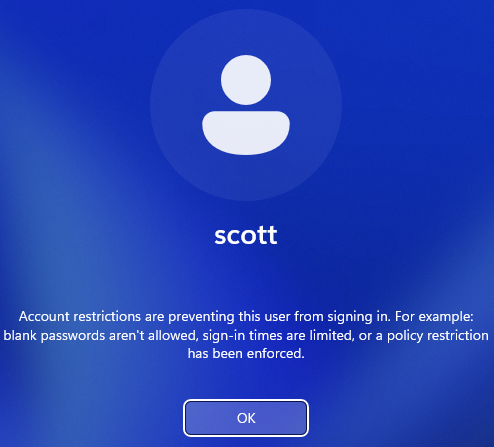
With everything set up, I rebooted my machine and…was immediately met with an error code.
How Can I Troubleshoot When I Can’t Sign In?
I was in a pickle. I needed to fix this problem without being able to sign in normally.
First I checked the DUO Admin Portal for logs using my phone. There was no log generated for this sign-in attempt, which tells me one of the following is the point of failure:
- The local application is misconfigured.
- There is a network point of failure between my workstation and DUO cloud. I have offline sign-ins disabled in my DUO policies, so a communication failure would prevent authentication.
- There is a misconfiguration server-side.
Always Check the Logs
I knew from workplace experience that the DUO endpoint application does store clear-text logs. They should get me closer to the problem.
I booted into the Windows Recovery Environment by holding the SHIFT key and selecting POWER > RESTART. Then, from the Recovery Environment, I launched into Safe Mode2.
Once in safe mode, I navigated to C:\ProgramData\Duo Security\duo.log and read through the data to find the issue.
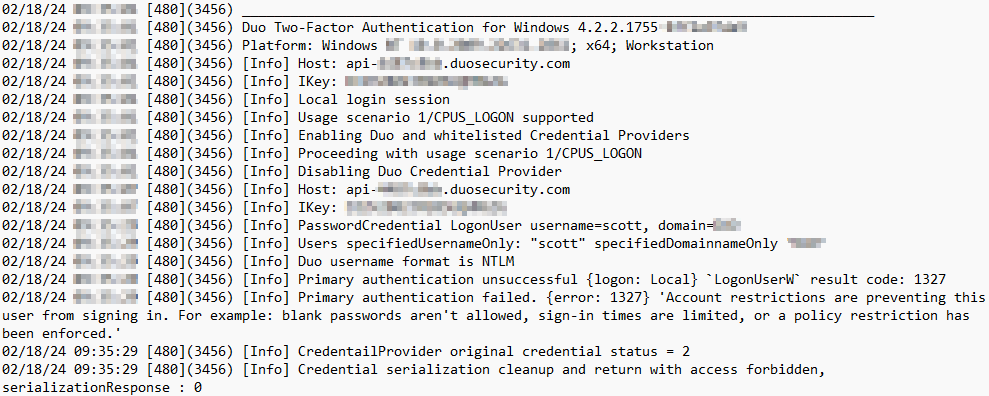
I could see that the API host and integration key were correct, so perhaps I had flubbed the secret key. I ran the below commands to disable DUO locally and then uninstalled the application after exiting safe mode and signing in normally.
regsvr32 /u "C:\Program Files\Duo Security\WindowsLogon\DuoCredProv.dll"
regsvr32 /u "C:\Program Files\Duo Security\WindowsLogon\DuoCredFilter.dll"I re-installed DUO, double-checked the secret key, and restarted. Same error.
I also updated the temporary blank password that I had to a proper password. No change in symptoms.
Firewall?
I repeated the above to escape my sign-in purgatory and set my sights on ruling out a communication failure between my desktop and DUO cloud since we’ve addressed the local application.
The simplest way to test this was to allow offline authentication in the DUO Policies server-side and locally (set during installation). If communication fails, we should see Windows bypass the check altogether and authenticate normally.
We did not.
So What is Wrong In DUO Cloud?
At this point, I felt a policy was to blame. For my Windows logon, two sets of policies are passed through: Microsoft RDP application policies, and the general DUO policies.
Microsoft RDP policies were simple to rule out. I simply set the application to Bypass Mode and gave it a whirl. I got the same error code, so I set my eyes on the general DUO policies.
With Microsoft RDP in Bypass Mode, I also set the general DUO Authentication Policy to bypass mode. I still got the same error… what was I missing?
Username
From the logs, I knew DUO was recognizing my username format as NTLM3 and parsing it into username and domain. For example, DUO will see a login for PCNAME\USERNAME and parse the credentials into two variables:
- specifiedUsernameOnly: “USERNAME”
- specifiedDomainOnly: “PCNAME”
Because I still saw no authentication logs (pass, bypass, or fail) in the Admin Portal, I set my sights on the user configuration.
Lo and behold, I had absent-mindedly set the username in DUO as “sjenkins” which was the local user on the PC before I did a re-image. The correct username is now “scott”. That means the authentication request DUO for Workstation was sending to my DUO API instance did not match any user and thus had nowhere to send a push to.
I added “scott” as an alias to my user and gave sign-in a final try.
The push was sent straight to my phone…

What a beautiful sight!